WikiLeaks: The CIA Can Covertly Activate Your Mobile Device’s Microphone, Bypass Encryption Apps 7 Mar 2017
Article from Breithbart
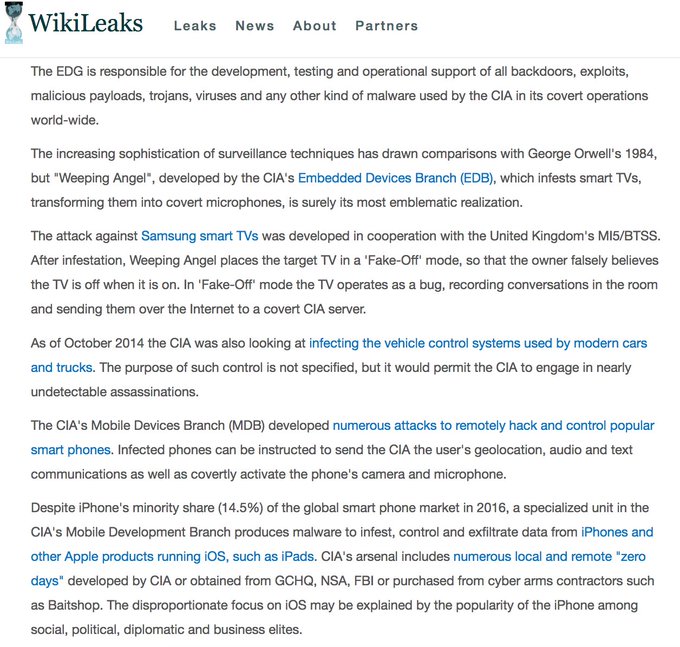
WikiLeaks’ “Vault 7” dump of information on the CIA’s hacking unit has revealed that the agency has the ability to hack mobile phones, TVs, and even computers that are not connected to the internet.
According to the files contained in “Year Zero,” WikiLeaks’ codename for the first batch of the CIA leak, the agency has malware that can infect iOS, Windows and Android devices. Crucially, this malware allows it to bypass encrypted communication apps favored by journalists, including Signal, Telegram, and Confide, as well as the popular messaging app WhatsApp.

WikiLeaks #Vault7 confirms CIA can effectively bypass Signal + Telegram + WhatsApp + Confide encryptionhttps://wikileaks.org/ciav7p1
Wikileaks later clarified that the CIA does not have the ability to crack the encryption itself, but is able to bypass it by directly hacking operating systems.
The CIA also has the ability to hack Samsung Smart TVs, turning them into covert microphones even when the device appears to be switched off. According to WikiLeaks, the CIA’s Mobile Devices Branch (MDB) can do the same to smartphones, which can also be instructed to transmit a user’s geolocation.
That Samsung smart TV? The CIA can turn the mic on and listen to everything you say #vault7 #1984rebooted
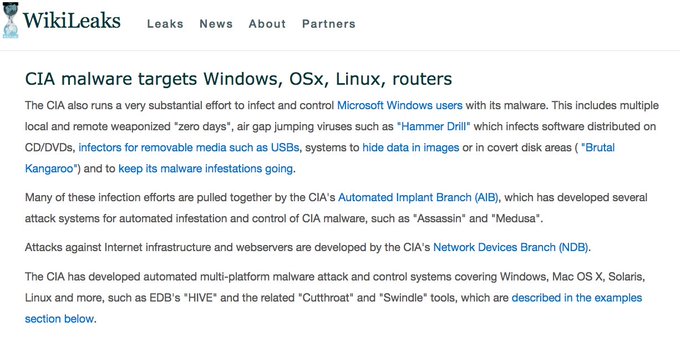
Furthermore, WikiLeaks also shows that the CIA is attempting to hack devices that are not connected to the internet, including those protected by the so-called “air gap” — a computing term used to describe measures that keep devices and networks disconnected from public networks including the internet.
WikiLeaks #Vault7 reveals CIA ‘zero days’ vulnerabilities Windows, CIA air-gap jumping viruses
Much of this vast hacking power is now in the hands of third parties as well as the CIA. According to the WikiLeaks, dump, the CIA has lost control of much of its hacking arsenal to unknown parties, after the cyber-weapons were “circulated among former U.S government hackers and contractors in an unauthorized manner.”
Recently, the CIA lost control of the majority of its hacking arsenal including malware, viruses, trojans, weaponized “zero day” exploits, malware remote control systems and associated documentation. This extraordinary collection, which amounts to more than several hundred million lines of code, gives its possessor the entire hacking capacity of the CIA. The archive appears to have been circulated among former U.S. government hackers and contractors in an unauthorized manner, one of whom has provided WikiLeaks with portions of the archive.
You can follow Allum Bokhari on Twitter and add him on Facebook. Email tips and suggestions to abokhari@breitbart.com.